These attributes, which ensure that all information are held intact, are ideal when vital metadata information need to not be modified, for example for regulatory compliance and archival purposes.
people who function with documents can specify how sensitive they are—they might accomplish that if they create the document, after a major edit or overview, or ahead of the document is introduced.
element: make use of a privileged entry workstation to reduce the attack surface area in workstations. These secure management workstations will let you mitigate Some attacks and be certain that your data is safer.
obtain to non-public data ought to be limited to persons having a “want to be aware of” and may be guarded using solid encryption and obtain controls. companies also needs to have guidelines in place to ensure that personal data click here is saved and disposed of securely.
Leverage Secoda’s automated data discovery to analyse discrepancies, giving produced stories with data issue drilldowns and insightful tips. put in place data principles and alarms to then identify errors in the data and eliminate them speedily, whilst also assessing data completeness.
And with plaintext website traffic, an attacker could possibly intercept it in transit and decrypt it later, especially if they have entry to an unpatched flaw within the protocol getting used.
AI’s problems and alternatives are worldwide. The Biden-Harris Administration will carry on dealing with other nations to aid safe, protected, and reliable deployment and usage of AI around the globe. To that conclusion, the President directs the next steps:
The concepts behind confidential computing usually are not new, but The supply of TEEs and confidential computing within the cloud ensure it is a lot more appealing to businesses that need to protected their data from application vulnerabilities. I recommend that enterprises explore using confidential computing tactics in the next six-12 months, and specify for their key software solution providers that they expect them to adjust to the confidential computing system and provide technological know-how implementations within the very same time period.
For virtualized EC2 circumstances (as proven in determine 1), the Nitro Hypervisor coordinates with the fundamental hardware-virtualization devices to develop virtual equipment which have been isolated from one another together with from the hypervisor itself. Network, storage, GPU, and accelerator accessibility use SR-IOV, a technology that allows instances to interact directly with hardware equipment using a move-through relationship securely designed from the hypervisor.
The scope In cases like this will be a subscription, a resource team, or simply just a particular vital vault. If the predefined roles Never fit your preferences, it is possible to outline your personal roles.
during the last 10 years, cloud computing has revolutionized just how the world computes. Many providers and companies have moved from devoted managed servers at Qualities they possess to versatile methods which can scale up or down according to the level of electric power and storage they will need at any given moment.
companies which might be weak on data classification and file safety may very well be extra prone to data leakage or data misuse.
To summarize, the Nitro program’s exclusive method of virtualization and isolation permits our consumers to protected and isolate sensitive data processing from AWS operators and software continually.
for almost any university student or worker working on a Princeton Pc, this would be the LDAP login ID and password that person was assigned at matriculation or Preliminary employment. For information on requesting LDAP login IDs and passwords for momentary workforce or consultants, Click the link.
 Jonathan Taylor Thomas Then & Now!
Jonathan Taylor Thomas Then & Now!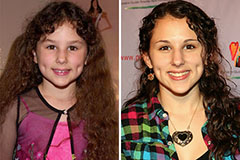 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Gia Lopez Then & Now!
Gia Lopez Then & Now! Bill Murray Then & Now!
Bill Murray Then & Now! Rossy de Palma Then & Now!
Rossy de Palma Then & Now!